On October 21st, the 2015 SyScan360 International Forward-looking Information Security Conference, known as the vane of international information security development, was held in Beijing. Excellent Internet security experts and top hackers from around the world showcased Asia's top security technologies. Among them, the safety of the Internet of Vehicles has become the focus of this information security conference. Qi Xiangdong, founder and president of 360, said that the combination of big data and network security technology can detect anomalies, capture threats, and realize rapid monitoring, discovery and response of threats and intrusions from a higher perspective and a broader dimension. "In the era of the Internet of Everything, security has broken through the boundaries of software, content, services, etc., and may be in crisis." Qi Xiangdong revealed that 360 has joined forces with a number of institutions and car companies to prepare for the establishment of the China Car Network Security Alliance to bring together the cyber security capabilities of the entire society to jointly address and solve the information system security of automobiles. In this conference, the famous hackers from the United States who just joined Uber, Charlie Miller and Chris Varasek, brought the latest research results. They will demonstrate a remote attack on an unmodified factory. car. They first showed that the CAN bus information was sent to the key electronic control unit using different hardware of the car, sharing some information that would affect the car's physical system, and finally introduced the practical problems and limitations of the long-range car attack. In July of this year, Miller and Wallacek used the in-vehicle information service system "UConnect" to successfully invade a Jeep Cherokee on the highway ten miles away, causing the car to fail and turn into the ditch. Since then, the threat posed by hackers has officially entered the life threat level. Subsequently, Chrysler announced the recall of about 1.4 million cars with software vulnerabilities, the first car manufacturer to recall the car because of hacking risks. Research on Chinese hackers in the field of car networking security is also worth mentioning. At the meeting, Liu Jianwei, a security expert from 360, demonstrated the results of the attack on Tesla and BYD and introduced the methods and tools. For example, the use of reverse communication protocols to exploit vulnerabilities, remote control of cars using the defects of car apps, and the latest research findings. The car has become a veritable "computer on wheels". In 2014, the computer on the car, at least 100 computers, running 60 million lines of code, exchange 25MB of data per hour. Intelligent and networked brings easy, economical, convenient, enjoyable and intelligent experiences such as smart navigation, autonomous driving, automatic parking, car and car connectivity, remote control, and driverless driving. However, because the computing and networking systems used in automobiles follow the existing computing and networking architectures, and inherit the natural security flaws of these systems, the automotive industry is facing an increasingly difficult information security situation in the PC and Internet sectors, hacking. Security vulnerabilities, car cracking and hijacking began to be associated with cars. In February 2015, the US General Motors OnStar system was exposed to security vulnerabilities, and hackers could use it to remotely control the car. 360 announced the discovery of a defect in the Tesla application. The attacker could use this vulnerability to remotely control the vehicle, unlocking and whistling. , flashing lights, turning on the sunroof, etc. The safety experts of the 2015 HackPWN Safety Geek Carnival Organizing Committee demonstrated the use of this security hole to open the car door, start the car, open the trunk and so on. BYD confirmed that the vulnerability exists. Frequent security breaches and hacking incidents indicate that car information system security is directly affecting car safety and endangering public safety, personal and property safety. "Traditional security protection has been unable to solve the security problem in the era of Internet of Everything!" Qi Xiangdong stressed that 360 proposes to use data-driven security to solve future security problems. By combining big data methods with modern network security technologies, through the recording, storage and analysis of various types of network behavior data, it is possible to discover anomalies, capture threats, and realize threats and intrusions from a higher perspective and a broader dimension. Rapid monitoring, discovery and response. It is reported that China Auto Network Security Alliance will promote automakers and related industry chains to fully consider information system security in design, development and testing, and promote the establishment of corresponding norms, standards and systems; promote cooperation between the automotive industry and the network security industry, and jointly Addressing evolving information system security issues; absorbing and helping third-party security researchers to participate in research and resolution of automotive information systems security issues.
Describe:
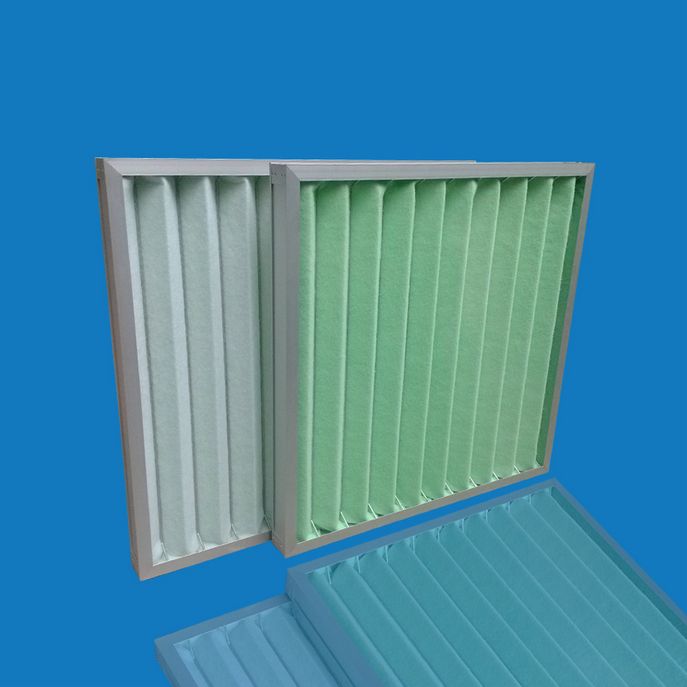
The primary filter is suitable for primary filter of air conditioning system, mainly used to filter dust particles above 5 μm. The primary filter has three styles: plate type, folding type, bag type, outer frame material has paper frame, aluminum frame, galvanized iron frame, Filter Material has non-woven cloth, nylon mesh, activated carbon filter material, metal hole mesh, etc. The protective net has double side spray plastic wire mesh and double side galvanized wire mesh.
Characteristics:
Low price, light weight, good versatility and compact structure,This efficiency filter, commonly used as a primary filter for air conditioning and ventilation systems, is also suitable for simple air conditioning and ventilation systems that require only one level of filtration.
Applications:
1. central air conditioning and centralized ventilation system prefiltration.
2. large air compressor prefiltration.
3. clean air return system.
4. local high efficiency filter prefiltration.
5. high temperature Air Filter, stainless steel frame, Summary of filtration efficiency of high temperature tolerance 250-300 ℃.
this efficiency filter, commonly used as a primary filter for air conditioning and ventilation systems, is also suitable for simple air conditioning and ventilation systems that require only one stage of filtration.
Primary Air Filters Sponge Air Filters,Primary Air Filters,Sponge Air Primary Filters,Plate Primary Filters Henan Sinofiltec Technology Co.,Ltd , https://www.airfilters.pl